With the increasing amount of cyber crime on the web one thing clear is that internet is not safe today. A survey which was organized by people from the industry states that most of the cyber crimes happen due to ease of access and carelessness for example weak passwords which are easy to break in.
Companies like Google, Microsoft, Dropbox etc. who own the web lodged so many complaints for such cases in-spite of continuous awareness campaigns. Following the pattern of OTPs which major banking systems follow, these web firms also went on the similar trend and came up with two step verification method so provide extreme security to make accounts least prone to the hijacks which were often reported.

Two step verification method which is still not popular is the new standard to provide a security layer to your web accounts. Under this two step verification, a user is asked to activate the service on his/her account along with registering a mobile number. So next time whenever the user log-in to a new device he/she shall be asked to enter his password as usual ( or an optional randomly generated string ) and a compulsory verification code that will be received on his/her mobile number which will be only valid for this session.

We strongly recommend every one to activate two step verification. Following is a step-by-step guide on how to activate two step verification on Google account similarly can be done on other web services.
- Visit your account page.
- Click on security on the left side pane.
- Select 2-step verification and click on edit.
- Get your mobile device verified with the Google account. First step is verifying the mobile number for two step authentication.
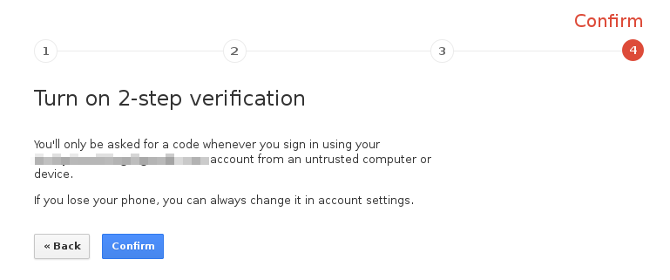
- After the verification process is done, you will be asked to keep this computer in trusted list or not. You may select that if you are using your own personal pc.
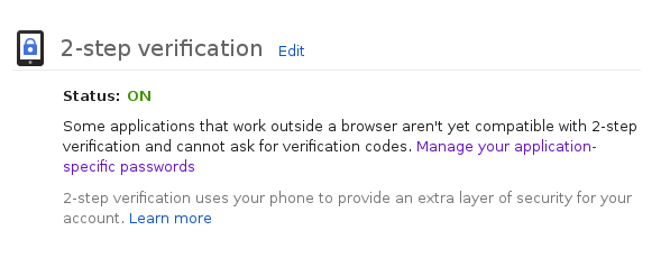
- And you are all set to go now. You have achieved two step security layer which keeps your account privacy and protects from attacks.

How did you like this tutorial? Leave us a comment below or on our Facebook Page or mention us on twitter. Any special requests are always welcome and we will be happy to help you.